Second time, is a charm
 Sniff, sniff! (♥‿‿♥) So many networks!!!
Sniff, sniff! (♥‿‿♥) So many networks!!!
What is a pwnagotchi?
Description:
Pwnagotchi is an A2C-based “AI” powered by bettercap and running on a Raspberry Pi Zero W that learns from its surrounding WiFi environment in order to maximize the crackable WPA key material it captures (either through passive sniffing or by performing deauthentication and association attacks). Source - https://pwnagotchi.ai/
Second time is a charm
Four years ago I found an interest with security in network, physical and wireless alike.
Overwhelmed by the copious amount of information on the subject, I struggled to get started and keep myself engaged.
I am not the standard type of human, I dont care about economical gains, only still my curious mind.
For the normal person, follow the cookie cutter steps and mindlessly fall into line by:
- Buy a course in on a famous global online learning platform
- Buy a certificate
- Post useless certificate on Linkedin and expect profit
Fuck that! I want answers…
So I keep asking questions, my doom and downfall…🤬
Pwnagotchi take 2
So what has changed? Well, now Pwnagotchi comes in 2 flavors apparently.
evilsocket/pwnagotchi
jayofelony/pwnagotchi
What you need
There is no specific rules and there are several different types of hardware you can use to create your pwnagotchi.
Parts I used
Raspberry Pi Zero 2 W - With header, because I am lazy
Waveshare v4 - 2.13inch e-Paper HAT (B)
PiSugar 3
Steps to get a running image on hardware
Requirements
I decided to try jayofelony/pwnagotchi flavour Since I wanted to try without AI and understand differences between the 2 flavours Which is funnier to use/tinker with?
Spoiler: I like evilsockets a little more, feels more like a tamagotchi You might want to check the release page, and choose a newer version. Since there is alot of updates and new features added all the time.
Download your 64-bit image by choosing the desired version to “Downloads” directory
URL: https://github.com/jayofelony/pwnagotchi/releasesIn the following steps, I am using version 2.9.4 of jayofelony/pwnagotchi
cd ~/Downloads wget https://github.com/jayofelony/pwnagotchi/releases/download/v[VERSION-NUMBER]/pwnagotchi-64bit.img.xzInsert device (storage medium) into usb slot, in my case a sd-card
Find device using lsblk - list block devices
$ sudo lsblk -o NAME,MOUNTPOINT NAME MOUNTPOINT sda └─sda1 /media/entropyasm/partitioned driveUnmount device using umount - unmount file systems
sudo umount /dev/sda1Uncompress the downloaded image using xz compress or decompress .xz files
sudo xz --decompress pwnagotchi-64bit.img.xzWrite data to the device using dd - convert and copy a file
sudo dd if=pwnagotchi-64bit.img of=/dev/sda status=progress
That is it! Unless you made any major changes, you will reach your pwnagotchi on port 8080 of the device ip
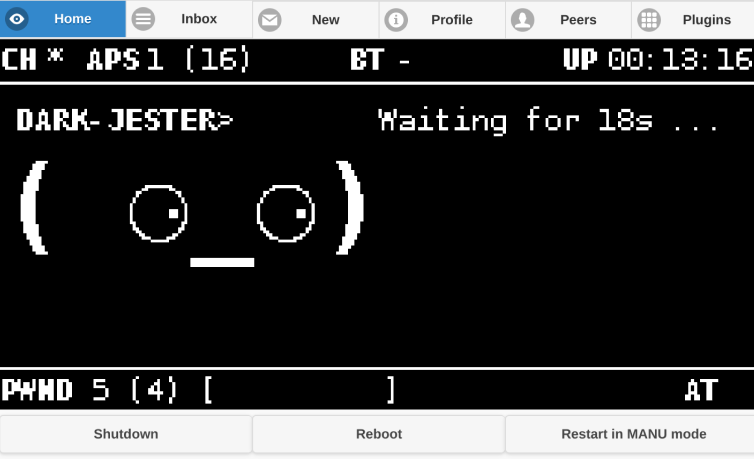
You can find the device ip with several services/apps “arp-scan”, “nmap” e.t.c.
Or just check your router’s DHCP service, to get the ip to your pwnagotchi
Example: using arp-scan
sudo arp-scan <adress>/<prefix> # CIDR adress, e.g. 192.168.1.0/24
Dance like nobody is watching!